Please note: this information is based on the most common forms of doxing we see in North America, but will vary by country. If you have information on how people from other countries experience this and feel like helping us expand this guide, please contact us!
IF YOU FEEL THAT YOU ARE IN IMMEDIATE DANGER, PLEASE CALL YOUR LOCAL EMERGENCY NUMBER
For everyone else, including those curious about doxing and those who have already been targeted, the following is a primer on the realities, pathology, and personal solutions for this particularly nasty form of online harassment.
What is doxing? Have I really been doxed?
Doxing (named for documents, or “dox”) is the public release of someone’s private information. Some argue over what constitutes a legitimate “dox” because of how freely available personal information is online, but at Crash Override, we use the following definition:
“Doxing is the act of publishing someone’s personal information, of which there would be a reasonable expectation of privacy and dubious value to the conversation, in an environment that implies or encourages intimidation or threat.”
This includes information that may arguably be easy to find, such as a home address from a WhoIs lookup or personal photos from Facebook, so long as it is wielded in a threatening manner - for instance, tweeted at someone in response to a disagreement. Doxing is less about the availability of the information, and more about the way it is used to intimidate or harass a target.
Of all forms of online harassment we observe at Crash Override, doxing is one of the most prevalent due to its relative ease and high emotional impact. For harassers, the pathology behind doxing is about rationalizing oneself as “blameless” for pawning off personal information for others to harass with. The person who paints a target on you might not be the one to act on it, but the message is clear: “I can’t be held responsible for what happens next.” Aside from intimidation, harassers will often use dox to create the illusion that they have totally invaded your personal space, even if their information is of limited value or inaccurate.
The most common response to being doxed is fear, if not outright panic. Feeling vulnerable is entirely understandable. Doxing is intentionally designed to violate your sense of security and cause you to panic, lash out, or shut down.
If you find yourself in this position, there’s a lot to consider. Our goal with this guide is to help you navigate your options and better understand your situation. Of course, if you feel you still need advice, please email us at help@crashoverridenetwork.com for personalized assistance.
I’ve been doxed - what do I do?
Before you do anything, remember that documenting your doxing is of the utmost priority. Things like screenshots, downloading the webpage, web archive (e.g. https://archive.org/web/ or http://archive.today/ - though it should be noted that using public services like this will make your dox viewable to others using that service), and other methods of record-keeping, preferably with things like timestamps and URLs visible, are crucial for both your own reference and for any third parties who may have an interest in your case. Not only does it create a chain of culpability, but the site of your doxing and surrounding threats can make it much easier to secure police or legal involvement should the harassment escalate.
This doesn’t mean you should leave your dox up if you can help it. Once it’s documented, sites like Pastebin, which are often used to share doxed information, have procedures in place (http://pastebin.com/contact) for removing private information. Twitter has also recently made doxing a violation of their TOS (http://gizmodo.com/twitter-just-banned-revenge-porn-and-doxing-1690916107), and accounts used to harass in this manner can often be reported and the offending posts removed.
If there is any important account information in your dox, we also highly suggest following our account security guide to keep your information safe and out of the hands of your harassers.
How should I react?
When you get doxed, panic can set in quickly. There is no “right” way to feel, as your state of vulnerability and what your personal information means to you is different from person to person. Whatever your initial response to being targeted may be—fear, anxiety, anger, confusion, helplessness–it is a valid and reasonable response to have in the face of such things. Don’t beat yourself up over it, and don’t worry about whether or not your reaction was the right one.
If you don’t feel you are at any great risk, and especially if your dox is comprised of freely-available information and/or sent directly to you in an effort to unnerve you, you may feel fine dismissing it as a cheap intimidation tactic, blocking/reporting the harasser, and moving on. This is often someone just trying to get a rise out of you. However, if your dox contains sensitive personal information, especially things that are hard for people to sniff out with simple detective work, or appears in a public forum where people distribute dox to have others act on it, you may want to take further precautions. This is especially true for marginalized people, especially in the case of trans people who have been deadnamed due to the greater risk of violence that trans people face in society at large.
Do I go public with it?
The first impulse you might have is to immediately alert as many people as you can with a public announcement - in fact, harassers usually intimidate their targets into not publicizing their harassment to deny them needed support. Officers will generally not tell you to stay silent about harassment. This is purely a victim-blaming and silencing tactic. The choice to go public and let people know about your doxing is a personal decision. Going public can expose you to immediate support if you have a sympathetic audience, but carries the risk of increased aggression from harassers. Not everyone has the time, energy, inclination, or freedom to bear further harassment (and, indeed, no one should have to).
There are some good arguments to be made for being initially cautious with information - While sharing your story can bring you support, the most important thing to do right now is to secure yourself in order to not expose yourself to further harm. Immediate announcements can trip up your security efforts - Whether or not the information posted about you is accurate, no one is likely to use it to cause you any serious harm without first confirming at least some part of it. Posting “I’ve just been doxed!” on a social media account immediately provides not only a confirmation that your information is accurate, but that you have seen where it was posted, and are properly terrified.
Denying the veracity of any information posted about you can be just as bad. This still confirms that your harassers have gotten your attention, and signals to them that they just need to keep digging. Sometimes, one of the most effective initial public responses is no response at all - don’t make any major changes to posting habits, or visibly show any fear if you can help it. This sends the message that your doxer probably missed the mark, and that the attack was a failure.
You should, however, prepare for more active efforts at verification. Usually, but not always, harassers will test the waters by calling whatever phone number is posted and asking to speak with you, or sending you emails/social media messages in hopes you’ll respond. Keep in mind, however, that with this sort of crowdsourced harassment, multiple unconnected parties may attempt this.
Evaluating Doxing Threats
Upon being made aware of a dox, it’s important to establish what information may translate into credible threats. Oftentimes, doxing is a precursor to more intrusive offline harassment, or comes paired with threats to act on the information revealed. The spillover could be anything from threatening phone calls and mail deliveries to pointed death threats or a SWAT call.
It is sometimes difficult to understand what makes a threat “credible” in relation to a dox. In order to be credible, a threat merely needs to inspire fear of safety by way of dox falling into the hands of people who may not be acting rationally or morally. The mindset of coming under credible threats is perhaps best outlined by this summation from a Reddit user (warning, NSFW language):
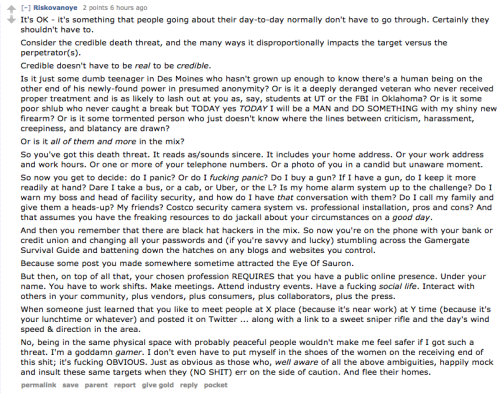
Creating this sense of panic is the typical end-goal of a doxing, but even if their intent is only to “harmlessly” ruffle your feathers, once the information is out there, it can pass under the nose of people willing to take it to new extremes. For this reason, it’s important to evaluate the information that they have gathered and the risks associated with that information in order to respond effectively. Any information pointing to your home address or financial information should be treated as a top priority, perhaps involving law enforcement if there are credible threats attached.
Responding appropriately can significantly reduce your stress and help you reclaim a feeling of control over your life. Focusing on hardening the areas they are attacking, and preventing them from ever finding the information they don’t have, can make the harassment you are receiving more bearable and prevent further escalation. Due to the crowdsourced nature of most online mobs and the bully mentality that drives them, “hard targets” are often quickly passed over.
Also, in evaluating your risk profile, the unfortunate truth is that online mobs are particularly vicious and persistent when their victim is a woman, LGBT (particularly trans), disabled, or belongs to a racial, ethnic, or religious minority. If you fit one or more of those elements the chances of someone acting on your dox increases substantially.
What follows is a cross section of the various kinds of information that diggers will collect, with a summary of how that information can be used:
- Home address: The highest risk factor, home addresses often lead to unwanted food deliveries, magazine subscriptions, missionary visits, and COD products, and carries with it the risk of SWATing or physical stalking, harassment, abuse, or assault.
- Finances/legal: Credit card numbers, banking information, social security numbers, anything of this sort should be reported immediately to the relevant institutions. Your bank, credit union, and law enforcement will recommend further actions you should take to protect yourself from further fraud and identity theft. Consider if your security questions could be answered by information now contained in your dox (like mother’s maiden name) and change it with your financial institution. Fortunately, these cases are rare, as harassment mobs try hard to avoid drawing too much scrutiny in order to prolong the harassment as long as possible, and openly committing credit card fraud is a great way to get federal agencies involved.
- Work/School: Harassment that bleeds over into your workplace or school can be particularly stressful, as abusers will seek to have you sanctioned or even fired by way of mass false reporting. Even without a specific accusation, this harassment can place your job at risk as some employers may find that firing you is simply less trouble than dealing with the harassment. Particular professions, notably those that rely on privileged confidence or involve working with children, are especially sensitive to accusations.
- Account Passwords: This becomes quite dangerous, especially if the account has access to reset other accounts or third party posting permissions. Often hijacked accounts are also used to impersonate you. Securing any compromised accounts should be a top priority, ideally adding two factor authentication to any account that supports it. If you suspect one of your accounts has been compromised, immediately attempt to recover it, change passwords, sign out all other sessions, and notify anyone who may have been contacted from it.
- Social Media Handles: Social media is principally used as a vector for further harassment and as a source of additional information. Generally dumping this information is somewhat redundant, as harassers have typically already honed in on these public channels as a means of abusing targets long before a doxing. While stressful, this information doesn’t represent a serious breach in and of itself. If more sensitive information was readily available through your social media (such as a phone number on a poorly secured Facebook account) then that info would have been posted as well. Generally respond to these by bumping up privacy permissions, using an auto blocker, so on and so forth. Avoid clicking any suspicious links you’re sent from unknown people, as harassers may be looking for confirmation of your handles or attempting to get you to download malware.
- Email: Typically this information will be used to send hatemail, signing you up for spam mailing lists, or using the address to register for embarrassing forums and services (filling your inbox with confirmation notices). A vulnerability that sets email apart from other social media, though, is that an email address that’s been used to sign up for lots of services, forums in particular, can lead diggers to additional information. Services such as Unroll.me and Mailstrom can help you quickly manage and unsubscribe from junk mail and clear up your inbox.
- IP Address: This is often used to find a target’s physical location. While this sounds severe, and does require your attention, a home IP address is of limited use outside of that unless an attack goes unnoticed for a significant time. Check with your Internet Service Provider about changing your IP address - often this is a simple request.
- Skype Handle: Skype handles should be treated with particular concern, as many cases we take at Crash Override stem from security holes in Skype and harassers using it as a vector to impersonate you to contacts, or single out said contacts for harassment themselves. Should this be the case, Microsoft thankfully offers live chat support (https://support.skype.com/en/faq/fa10656/what-is-live-chat-support) that allows a representative to freeze your account and return control over to you in short order. Additionally, linking your Skype account to a Microsoft account will allow you to enable two-factor authentication.
- Biographical Info: What high school you attended, your sexual history, previous forums you visited, dumb things you said as a teenager; This is a catch all for information that isn’t directly useful, but can be used to embarrass, slander, or shame you. Details like these are also used by “diggers” to cross reference other information. Depending on the severity and nature of the information, this can translate from a quick episode of doxing to an extended slander campaign as harassers attempt to promote your dirty laundry, no matter how innocuous, untruthful, or irrelevant it may be, simply to get a rise out of you.
- Phone Number: An especially obnoxious means of harassment, this will typically result in spamming you with text messages or harassing phone calls at all hours of the day. These may come from the abusers themselves, or from services that they may sign your number up for. In especially prolonged cases of harassment, the only means of alleviating this could be changing your phone number. However, law enforcement has an easier time investigating and prosecuting harassment by phone than it does harassment online, so be sure to document everything if you plan on going this route.
- Deadnaming: Deadnaming is a particularly vile and callous form of direct harassment wherein the mob digs up and in some way weaponizes a target’s former name. This is most commonly (though not exclusively) used against transgender individuals, whose birth names can be a source of anguish, or even professional and physical danger. While other doxed information might be passed around for others to act on, harassers will often use a dead name to directly bombard a target to cause them distress. In some cases, we’ve seen things like harassers registering sockpuppet accounts with someone’s dead name and then following their friends on social media. Many social media networks do not consider this a violation of their TOS despite the direct intent to cause suffering, and we are advocating for more networks to address this issue.
Should I wait until I’m doxed to contact the police or family?
If you’ve been doxed (or fear being doxed), the natural extension of that fear is that tangible harassment is not far behind, more so if you’ve been targeted by a group with a history of employing SWAT calls or physical intimidation. Depending on how much information you have about the people targeting you, the police may be of limited use; if all you have is a premonition, they may not be useful at all. However, if the dox is surrounded by any sort of credible intent to follow up on your information, especially specific threats of assault, death, or fraudulent police reports, do not hesitate to contact your local police. We have produced a guide for talking to family and the police about online abuse if you'd like advice on that.
If the dox does not have any credible followup attached, this is not to say that the situation you are faced with is any less harrowing, or that people may not follow up on the dox. In this stage, self-care, informing relevant parties, and enacting personal security are safe and effective ways to regain control of your life.
Should I Go Offline?
One stubbornly persistent attitude about online harassment is that the victim can “just step away” or otherwise disengage at any point to stop the harassment being committed against them. This is patently false, and again, a victim-blaming tactic - once harassers have you in their crosshairs, their “win condition” is highly situational. Some seek to simply silence you, others to provoke a visible reaction, some to ruin your life and reputation or even cause you physical harm. There might not be a “correct” action in any case, and no guarantee that harassers will stop, especially while your dox are still accessible. If you do step away, it should be a personal decision enacted for reasons of self-care.
Stepping away from online spaces can feel like admitting defeat, like your harassers “won” and have driven you off the Internet; such is the psychological trap abusers intentionally create. Laying low for a while is no different than creating some distance in a high-friction relationship, or taking time off from a stressful job. You have the right to feel safe in social spaces, and you have the right to back away from those spaces.
We often find that cases that benefit from “stepping away” involve people who are targeted incidentally or don’t provide their aggressors with any “entertainment value” from being doxed, leading the mob to move on because of diminished returns on their harassment. However, this also encourages the same aggressors to return to doxing as a strategy any time they want to silence their target. Losing the attention of harassers in this fashion should be treated as an opportunity to harden defenses, such as removing dox from websites and taking countermeasures like registering for WhoIs privacy or in severe cases, changing things like phone numbers/emails/address.
In other cases, there is a fear that stepping away may cede a narrative to your harassers. This is usually when the harassment is taking the form of a prolonged campaign of libelous or embarrassing dox across social networks, as opposed to merely bombarding you with abusive emails, magazines, or pizza deliveries. These situations may be severe enough that they benefit from active monitoring to better ensure that you do not return to a reputation in tatters. Should this happen, do not feel bad about asking others to monitor your social media for anything worrisome - you should not feel forced to subject yourself to psychological abuse out of fear alone.
My dox contains my address/credible threats. Should I leave my home?
If you ever feel unsafe in your home, do not feel bad about choosing to vacate it for any length of time. It is not an overreaction to remove yourself from the potential of harm if there is good reason to believe your security may be compromised, and labeling your actions as such is a form of victim-blaming. It is your choice to make based on your own standards, beliefs, and justifications.
In extreme cases, law enforcement may even recommend leaving your home. If this is the case, they will oftentimes work with you, or at the very least dispatch offers to your location in a protective capacity.
Summary
As has been mentioned, this guide is meant to be a high-level informative primer on the realities, consequences, and considerations of being doxed. Attitudes about what to do and how to go about it can differ by culture, region, ethnicity, gender, and myriad other factors - but hopefully, this guide can give you a sense of direction or comfort in the current environment.
If you find yourself facing coordinated online mob harassment, we welcome you to contact us at help@crashoverridenetwork.com, in hopes that we can better direct you to appropriate resources, advice, and practical knowledge. No two cases are the same, and common wisdom can often be inapplicable to your particular climate of online discourse and moderation. You are the best judge of your own needs and circumstances, and our hope is to empower you to make informed decisions when the time comes. You are not alone.